GLPI Documentation
On this page you can find all GLPI documentation
GLPI Administrator
Install & Update
Command line tools
Timezones
Advanced configuration
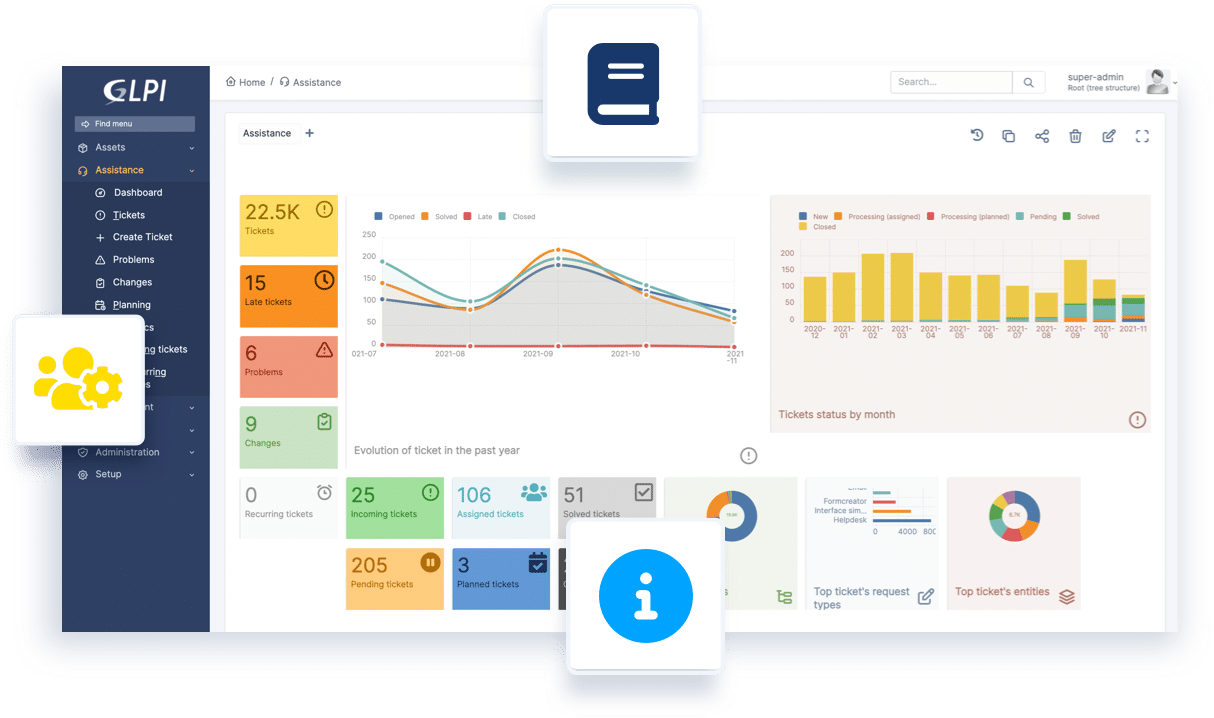
GLPI User
First Steps with GLPI
Overview of all modules
Configuration & Administration
Plugins & Marketplace
GLPI Developer
Source Code management
Coding standards
Developer API
Plugins Guidelines
Packaging
GLPI Agent
Installation (Windows / Linux / Mac OS / Source)
Configuration / Settings
Usage / Execution mode
Tasks / HTTP Interface / Plugins
Bug reporting / Man pages
GLPI Plugins
Community plugins
GLPI Network plugins
Contribute to documentation:
Professional support for GLPI:

GLPI ON-PREMISES
Install and configure!
Starting from 100 € per month.

GLPI NETWORK CLOUD
Sign up and start working!
19€ per IT agent*/per month


















